Blacklock PTaaS
As SaaS platforms become more complex and interconnected, traditional security approaches are no longer sufficient. Modern applications rely on APIs, open-source libraries, third-party services, and rapid deployment pipelines—all of which introduce new attack vectors. To stay resilient, organizations must adopt continuous security validation rather than relying on periodic audits.
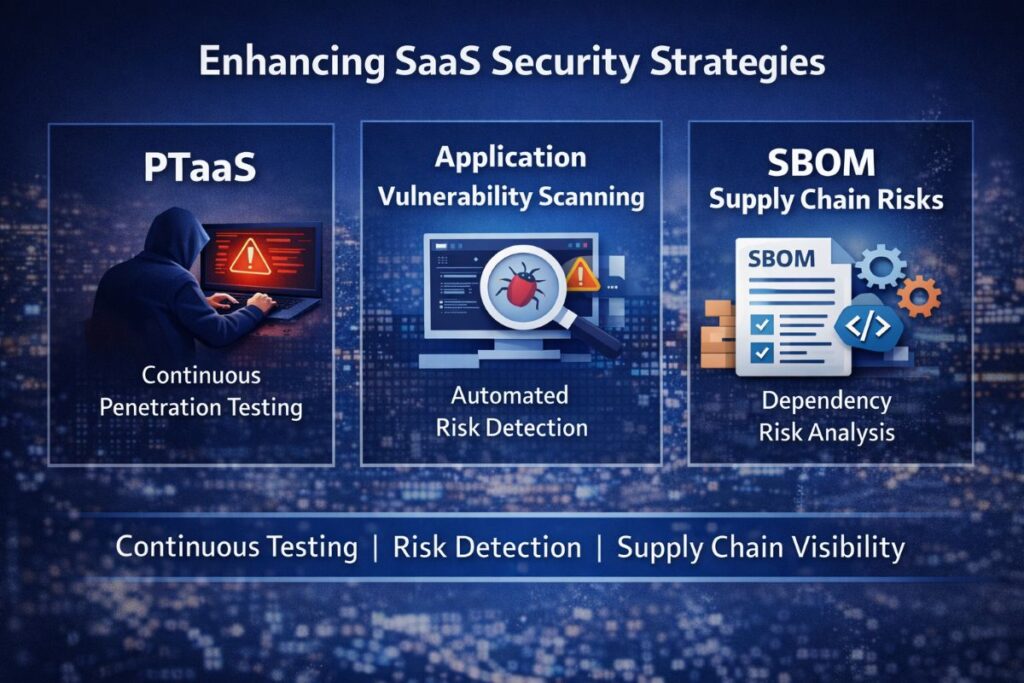
This shift has given rise to scalable security models that combine automation, real-world testing, and deep software visibility. Penetration Testing as a Service (PTaaS), application scanning, and supply chain risk analysis are now essential components of an effective SaaS security strategy.
The Evolution of Penetration Testing in SaaS
Traditional penetration testing often followed a point-in-time approach—conducted annually or after major releases. While valuable, this model struggles to keep up with agile development cycles and continuous deployment environments.
This is where Blacklock PTaaS introduces a more adaptive security model. PTaaS enables ongoing testing, real-time reporting, and faster remediation cycles, allowing security teams to align testing with business velocity.
Key advantages of PTaaS include:
- Continuous visibility into evolving security risks
- Faster validation after code changes or deployments
- Centralized dashboards for tracking vulnerabilities
- Improved collaboration between security and development teams
By moving from static testing to an ongoing security posture, organizations significantly reduce their exposure to exploitable weaknesses.
Why Application-Level Security Requires Continuous Attention
Applications remain one of the most targeted layers in SaaS environments. From authentication logic to data handling workflows, attackers focus on exploiting flaws that bypass perimeter defenses.
Application Vulnerability Scanning plays a critical role in identifying these weaknesses early. Unlike manual testing alone, automated scanning enables continuous coverage across web and cloud-native applications.
Effective application scanning helps organizations:
- Detect known vulnerabilities and misconfigurations
- Identify insecure dependencies and outdated components
- Monitor security posture across development stages
- Reduce the risk of exploitable production flaws
When integrated into CI/CD pipelines, application scanning becomes a proactive safeguard rather than a reactive fix.
Addressing the Hidden Risks in Software Supply Chains
Modern SaaS platforms are rarely built from scratch. Open-source frameworks, third-party libraries, and vendor integrations accelerate development—but they also introduce risks that are often invisible without proper tooling.
High-profile breaches in recent years have demonstrated how vulnerabilities in a single dependency can compromise thousands of organizations downstream. This has placed renewed focus on software supply chain security.
SBOM Supply Chain Risks Scanning provides organizations with transparency into the components that make up their applications. By analyzing Software Bills of Materials (SBOMs), security teams can quickly identify vulnerable or compromised dependencies.
Benefits of SBOM-driven scanning include:
- Faster response to zero-day vulnerabilities
- Improved compliance and audit readiness
- Reduced exposure to third-party risks
- Better decision-making around software dependencies
As regulations and industry standards increasingly emphasize software transparency, SBOM scanning is becoming a foundational security practice.
Connecting Testing, Scanning, and Business Risk
Cybersecurity is no longer just a technical concern—it directly impacts business continuity, customer trust, and brand reputation. A single application breach can lead to financial losses, regulatory penalties, and long-term damage to market credibility.
By combining continuous penetration testing, application scanning, and supply chain visibility, organizations gain a more accurate understanding of their risk landscape.
This integrated approach enables businesses to:
- Prioritize vulnerabilities based on real-world impact
- Align security investments with risk reduction goals
- Improve communication between technical and executive teams
- Demonstrate due diligence to customers and regulators
Security metrics become more actionable when they are tied to business outcomes rather than raw vulnerability counts.
Why Continuous Security Models Are the Future
Static security assessments struggle to keep pace with modern SaaS development. Cloud-native architectures, microservices, and frequent updates demand security solutions that evolve alongside applications.
Continuous testing models support:
- Faster innovation without sacrificing security
- Reduced remediation costs through early detection
- Stronger alignment between DevOps and security teams
- Better long-term risk management
Organizations that adopt continuous security practices are better positioned to scale securely while maintaining operational agility.
Blacklock Security Limited’s Approach to SaaS Protection
Blacklock Security Limited supports SaaS organizations by delivering modern security testing solutions designed for dynamic environments. Their approach emphasizes clarity, efficiency, and measurable risk reduction rather than checkbox compliance.
By leveraging continuous testing methodologies and advanced scanning techniques, Blacklock Security Limited helps organizations:
- Identify exploitable risks across applications and APIs
- Maintain visibility into software dependencies
- Improve remediation timelines through actionable insights
- Align security strategies with business priorities
This structured yet flexible approach allows companies to strengthen security without slowing down innovation.
Creating a Sustainable Security Strategy
Effective SaaS security is not built on tools alone—it requires process maturity, accountability, and strategic alignment. Organizations that succeed in reducing cyber risk treat security as an ongoing program rather than a one-time initiative.
Key elements of a sustainable strategy include:
- Regular security testing aligned with release cycles
- Clear ownership of vulnerability remediation
- Integration of scanning into development workflows
- Ongoing evaluation of third-party and supply chain risks
When these elements work together, security becomes an enabler of growth rather than a constraint.
Conclusion
As SaaS ecosystems grow more complex, security strategies must evolve to match the pace of innovation. Continuous penetration testing, application vulnerability scanning, and supply chain risk analysis are no longer optional—they are essential for protecting modern digital platforms.
Organizations that invest in visibility, automation, and real-world testing gain a significant advantage in resilience, trust, and long-term success.